Page 11 - Campus Chronicles Technical Magazine 2021
P. 11
• website pages on the Internet require no Application Security Risks
authentication or authorization. Authorization is From the large-scale network to centered database
supported on standard SQL but some special types altering of web apps the security issues are distributed.
of authorization are not supported like all There are some security risks below:
employees can see their own salary slip but not the Abstraction inObject
salary slip of anyone else in the company. This type • · The first security risk known as cross-site
scripting (XSS) permits an attacker to introduce
of authorization leads to a problem in SQL and the Oriented Programming
problems are client-side code into a site page. The attacker gets
direct access to the user's data. Using C++
• Less amount of information about end-user:
With the development of the Web, the access of the • Denial-of-service (DoS) and Distributed denial-of- By Ms. Poonumalli Harshitha,
database comes fundamentally from Web service(DDoS) attacks are used by some isolated
application servers. The end-users commonly try attackers to flood a designated server or the B. Tech (CSE) - 19UP1A0589
not to have unique client identifiers on the actual framework that upholds it with different sorts of
database, and for sure there may just be a single traffic. This traffic in the end keeps real users from
client identifier in the database compared to all getting to the server, making it shut down.
users of an application server. Accordingly, • A strategy called SQL injection (SQLi) is used by
authorization determination in SQL can't be hackers to take advantage of database flaws.
utilized in the above situation. These hackers, specifically, can uncover user Data Abstraction is a process of providing only the Abstraction in header files: An another type of
personalities and passwords and can also create, essential details to the outside world and hiding the abstraction is header file. For example, pow() function
• Absence of fine-grained authorization: internal details, i.e., representing only the essential available is used to calculate the power of a number
Authorization should be at the degree of individual modify and delete data without taking permission details in the program.Data Abstraction is a without actually knowing which algorithm function
tuples if it is to be approved that employees can of the user.
see just their own salary slip. Such authorization is • When a hacker executes a variety of attacks on an programming technique that depends on the uses to calculate the power. Thus, we can say that
unimaginable in the current SQL standard, which application and ends up accidentally changing seperation of the interface and implementation details header files hides all the implementation details from
licenses authorization just on a whole connection some spaces of memory then Memory corruption of the program.Let's take a real life example of AC, the user.
or view, or on determining attributes of relations or occurs. As a result, the software can behave which can be turned ON or OFF, change the
perspectives. normally or shut down at the end. temperature, change the mode, and other external Access Specifiers Implement Abstraction:
components such as fan, swing. But, we don't know the • Public Specifier: When the members are declared
• Privacy: Privacy is the part of information • The buffer overflow happens when corrupted code internal details of the AC, i.e., howit works internally. as public, members can be accessed anywhere
technology (IT) that deals with the capacity an is introduced into the system's memory. Thus, we can say that AC seperates the implementation from the program.
association or individual needs to figure out what Overflowing the buffer zone's ability causes a details from the external interface. • Private Specifier: When the members are
information in a computer system can be shared neighboring region of the application's memory to declared as private, members can only be
with third parties. Applications that access such be overwritten with data, representing a security In C++ program if we implement class with private and accessed only by the member functions of the
private information should be built cautiously, risk. public members then it is an example of data class.
remembering the privacy regulations.
abstraction.
Advantages Of Abstraction:
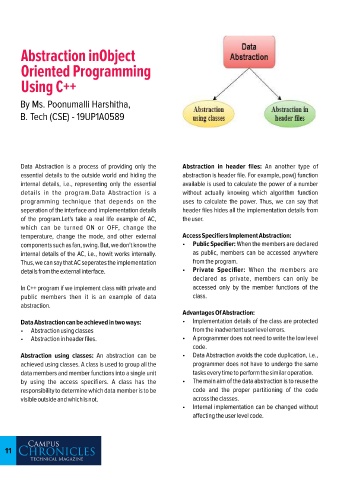
Data Abstraction can be achieved in two ways: • Implementation details of the class are protected
• Abstraction using classes from the inadvertent user level errors.
• Abstraction in header files. • A programmer does not need to write the low level
code.
Abstraction using classes: An abstraction can be • Data Abstraction avoids the code duplication, i.e.,
achieved using classes. A class is used to group all the programmer does not have to undergo the same
data members and member functions into a single unit tasks every time to perform the similar operation.
by using the access specifiers. A class has the • The main aim of the data abstraction is to reuse the
responsibility to determine which data member is to be code and the proper partitioning of the code
visible outside and which is not. across the classes.
• Internal implementation can be changed without
affecting the user level code.
Campus Campus
CHRONICLES 10 11 CHRONICLES
Technical Magazine Technical Magazine